A secure and manageable interface is all that we need.
Being an engineer, developer, manager, or any IT freak, security and manageability is the priority in the list of necessities. I hope you will affirm this corollary. Security in IT comes from building a wall of protection in front of our software, data, project, or anything that is protectable. A firewall works as that wall of protection, and AWS WAF works as a firewall for web applications. So, if the security of your most valuable web application is your concern, you will be holding grip till the end of this blog with me. Don’t worry. You will get clarity over every point till the end.
AWS WAF:
As the name explains, the AWS web application firewall works as a firewall for a web application. It helps to protect your web applications from bot attacks, unusual incoming traffic, and various exploits that cause security damage, valuable data consumption, and functional speed lag.
Let me elaborate with an example. Suppose for a while that you owe a multi-billion company that entirely functions offline. You will hold various files containing valuable data, security passes, profit and loss statements, company policies, and plans, and you will surely not like to keep it public. You will need a security guard outside your office who verifies the identity of the people trying to excess in the room where data is stored. You will make some rules based on which the guard will give access or deny someone to enter the office. The same goes here.
AWS web application firewall holds three things that make it work: An Access Control List (ACL), rules, and rule groups. Based on these control lists and rules, AWS WAF provides access to or blocks some requests called.
It allows control access to the content by tracking IP addresses of the origin of the request, or it tracks request query string values. If the request is allowed, it grants access and returns the requested data, but in the case of blocked requests, it responds with a status code of 403 (i.e., forbidden access).
Build Your Career as a
AWS Solution Architect
- Live Projects
- Resume / Interview Preparation

Features of AWS WAF:
- Time efficiency: AWS provides you with various prebuild sets of rules which you can access directly, like Open Web Application Security Project (OWASP) Top 10 security risks, threats specific to Content Management Systems (CMS), or emerging Common Vulnerabilities and Exposures (CVE). Pre-managed rules save a lot of time and give you an upper hand for indulging more in development.
- Agile protection method: Based on the generated rules, AWS WAF protects the web application. The prebuild rules provided by AWS help in most of the possible security needed from bots and other security attacks. We have the opportunity to filter any part of web requests like HTTP headers, URI strings, and IP addresses. These properties signify it to be the agile method of protection of web applications.
- Web traffic visibility: AWS web application firewall provides real-time visibility towards the traffic, which gives us an enhanced way to handle web traffic.
There are many more features of using Amazon WAF, like the easiness of development and maintenance, monitoring and limiting bots, and security integration. You can learn more about these by exploring our blogs and courses, which are well-designed for you.
Boost your earning potential with AWS expertise. Explore our certified AWS Courses for a high-paying career
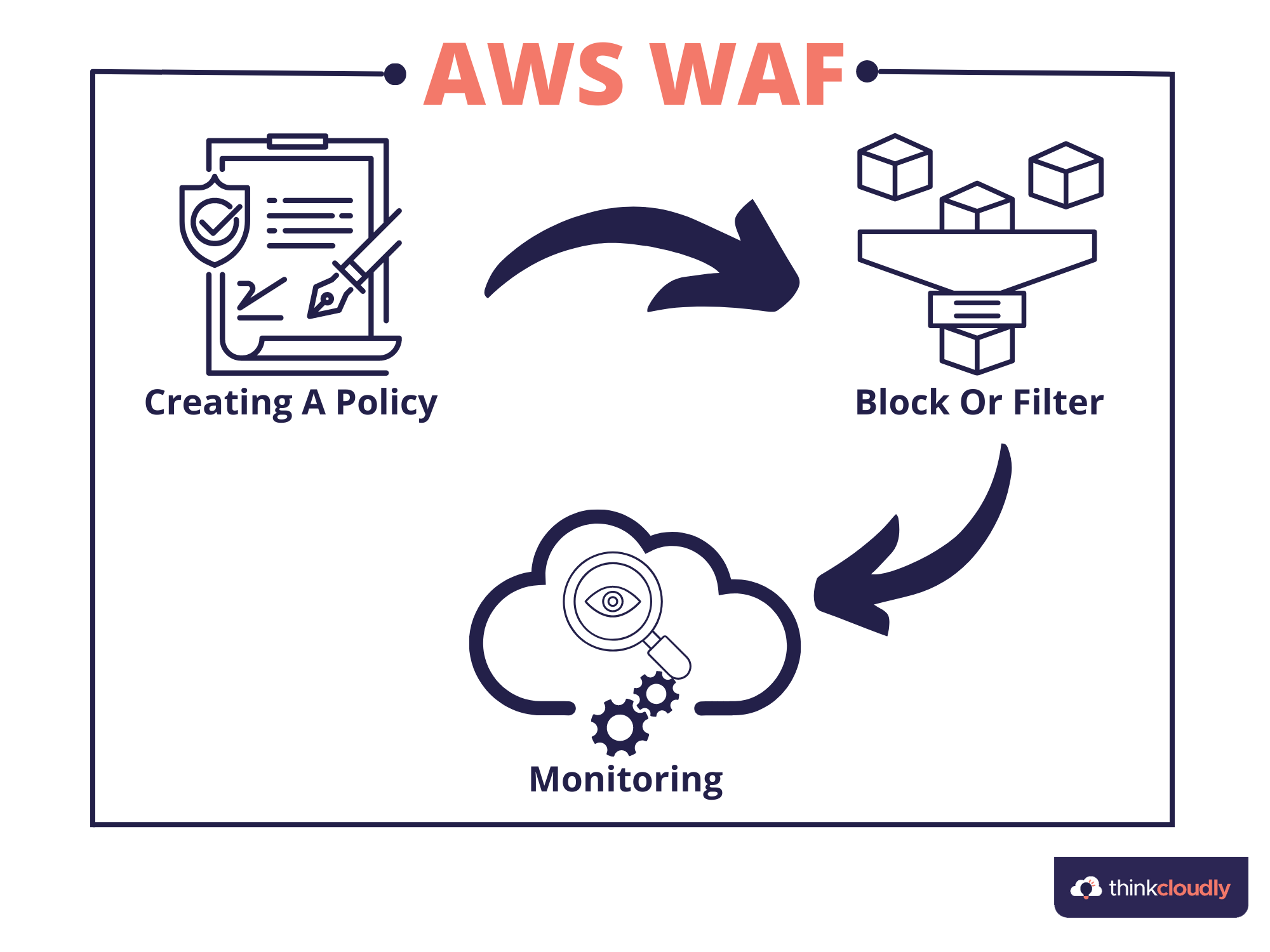
Working of AWS WAF:
The working schema goes into three simple steps: creating a policy, blocking and filtering, and monitoring.
- Creating a policy: The first step is building our own rules based on which the request is either granted or blocked. You can also use rules provided by AWS or the sellers at the AWS marketplace.
- Block or Filter: This is the step in which a request is either blocked, and the code for forbidden access gets projected, or the access is permitted with the projection of requested data. The decision of blocking or filtering the request gets performed based on a designed set of rules.
- Monitoring: Using various tools provided like Amazon CloudWatch and Amazon Kinesis Firehose for incoming traffic metrics and request details, respectively, the various requests can be monitored, and a specific result got taken out to implement forward.
Based on these three steps Amazon WAF works and results in such helpful outcomes.
Starting up with AWS:
AWS provides many more valuable tools at a very genuine and affordable price. I have mentioned three basic steps to follow to start with AWS, while AWS is an ocean of things to do. You can learn those all and move your hands like an expert by exploring our courses. Explore Now!
- The first step is signup by putting in your credentials for an AWS account.
- You can refer to 10-15-minute tutorial videos explaining the essential things to work with on AWS.
- You are all set to go. Start building your environment of cloud with AWS.
Key points to take home:
- AWS web application firewall works as a firewall for a web application. It helps to protect your web applications from various bot attacks, unusual incoming traffics, various exploits that cause security damages, consumption of valuable data, and lag in operating speed.
- AWS web application firewall holds three things that make it work: Access Control List (ACL), rules, and rule groups.
- Amazon WAF’s three main features are time efficiency, agile development method, and web traffic visibility.
- The whole working model follows three significant steps: creation of policy, blocking and filtering, and monitoring.
This content was all for this blog. I hope you got crystal clear information on one more topic in AWS. Please drop your comments for your queries or reach out. We are waiting for you at Thinkcloudly. See you soon.