What if any third party monitors your messages on WhatsApp to your friend?
What if your company expense chart is public on social media?
Do you have ever exclaimed what does end to end encryption of messages signifies?
If yes, then this blog is going for you. Cryptography comes into the game to keep your messages secure and accessible only to you and the authorized receiver.
Cyberattacks are very prone nowadays. Attackers are waiting for any loophole to play with you and your data every moment. One kind of cyberattack takes place while you share any data or messages. We transfer encrypted data from sender to receiver to secure these kinds of data. I will be explaining everything in this blog. Keep reading.
Cryptography
Cryptography transfers encrypted data and decrypts the received data in a readable format. The definition seems a bit confusing to you. Don’t worry. Let me simplify this for you.
Firstly, let us understand some basic terms:
Plaintext: Plaintext is the normal text that has to be transferred from an authorized sender to the authorized receiver.
Ciphertext: Once the plane text is encrypted using some algorithm, it is converted to ciphertext. The ciphertext is not readable by any attacker as he needs to know the decryption algorithm and key for converting it to a readable format.
Encryption: Encryption converts plaintext into ciphertext using a pre-described algorithm and a key.
Decryption: Decryption is a process of converting ciphertext into plaintext.
Firstly, the plaintext is converted to the ciphertext using an encryption algorithm, and then the ciphertext is transferred to the authorized receiver. The receiver converts the cipher text to plaintext using a decryption algorithm. This process of transferring the data is termed Cryptography.
Boost your earning potential with Cyber Security expertise. Explore our certified Cyber Security courses for a high-paying career
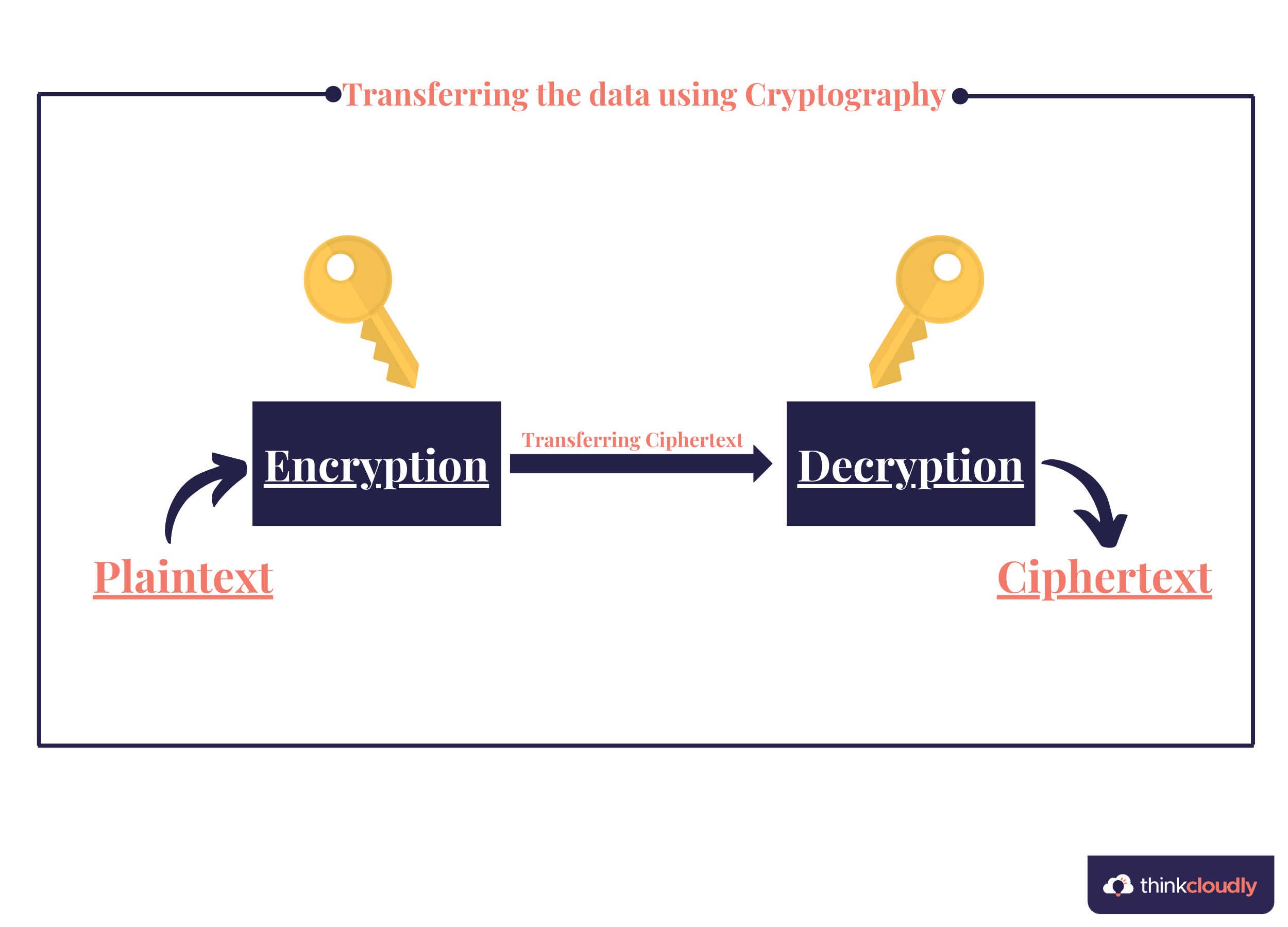
Transferring the data using Cryptography
The data is transferred using the pre-designed method. The whole transfer goes on in 3 major steps:
- Encryption: The initial step is to encrypt the data or message. Let’s say a plaintext is transferred. If any attacker gets any access while sharing the data, you will be vulnerable to attack, and so will your private data. The encryption process follows the various encryption algorithms to encrypt the data. Once the data is encrypted, it is not normally readable. The attacker will need to know the encryption algorithm and the key to decrypt the data, which is nearly impossible at the same time to access both things.
So, previously as the attacker only needed to embed the transferring system to get the data, now using the concept of cryptography, he will first embed to get the cipher text. Still, he will need the encryption algorithm and key, and that’s why our data is secured.
- Transferring of ciphertext: This is the normal process of data transfer which can be done using any transferring medium. As the data is now encrypted, we are now secure, as even if an attacker gets access, he will only get the ciphertext in his hand.
- Decryption: Decryption is a similar process to encryption but serves a different purpose. Unlikely encryption decryption uses the decryption algorithm and the key to convert the received cipher text into plaintext. The notable thing is that the keys in the scenario of encryption and decryption can be similar or different depending on the algorithm used but will be known to the authorized person.
In some aspects, we even use a public key, which means a key value known to everyone, but still, we have the security of data. Interesting, isn’t it? That depends on the different types of algorithms we have in cryptography. You can play with these algorithms. Explore our detailed course on cybersecurity now!
Brute Force Attack
At every point where there is security, there is a point of attack. So do here. Even if we use such encryption algorithms and keys to encrypt the data, the algorithms are limited and public, so the point of security comes on keys. The attackers used to make millions and millions of guesses to track the key, and with the modern computer, it has become an easy task. So even after that much security, there is a possibility of attack. This attack is called Brute Force Attack and, more specifically Brute force attack of encryption.
Even such attacks are tackled using much more complex and randomly generated keys. The hash key is one of the rising examples.
Points to take home
- Cryptography transfers encrypted data and decrypts the received data in a readable format.
- Encryption is converting plaintext into ciphertext using a pre-described algorithm and a key. Decryption is a process of converting ciphertext into plaintext.
- The data is transferred using the pre-designed method. The transfer goes on in 3 major steps: encryption, transferring, and decryption.
- The attackers used to make millions and millions of guesses to track the key, and with the modern computer, it has become an easy task. So even after that much security, there is a possibility of attack. This attack is called Brute Force Attack and, more specifically Brute force attack of encryption.
- Explore the world of cryptography with many interesting algorithms with courses on cybersecurity.





No comment yet, add your voice below!