As mentioned in the title, we will discuss legacy authentication, what it is, why we should block legacy authentication, and how to do it. Let’s begin!
Blocking Legacy Authentication: Strengthening Security Measures
Enabling a policy to block legacy authentication is a proactive security measure aimed at bolstering the protection of modern authentication methods. By implementing this policy, organizations can prevent users from utilizing outdated and less secure forms of authentication, which are often targeted by cyberattacks. Legacy authentication encompasses methods like NTLM and basic authentication, which lack the robust security features of modern approaches like multi-factor authentication (MFA). Implementing a policy to block legacy authentication aligns with best practices in cybersecurity, reducing the attack surface and enhancing the overall security posture of an organization’s digital assets.
In today’s ever-evolving cybersecurity landscape, it is imperative to bolster your organization’s defenses against potential threats. One highly effective measure is to enable a conditional access policy that can block legacy authentication methods. Legacy authentication protocols, often outdated and less secure, can pose significant vulnerabilities. By implementing such a policy, you can ensure that only modern and more secure authentication methods are permitted, thereby enhancing your organization’s overall security posture. This proactive approach is crucial in safeguarding sensitive data and maintaining a robust security environment.
What is legacy authentication?
Legacy authentication protocols are the basic protocols used by old office client applications. These are authentication methods commonly used by mail protocols such as IMAP, SMTP, POP3, Autodiscovery, etc. These protocols are mainly used by old office365 client applications such as Outlook 2010.
These protocols do not support or enforce Multi-factor authentication attackers, therefore, prefer these entry points to attack your organization.
The below protocols are considered legacy authentication protocols.
- Authenticated SMTP
- Exchange Online PowerShell
- Exchange Web Services
- IMAP
- MAPI over HTTP
- OAB (Offline Address Book)
- Outlook Anywhere
- Outlook Service
- POP3
- Reporting Web Services
- Other clients
Why do we need to block legacy authentication?
- 99% of password spray attacks happen using this protocol
- The legacy protocols do not support MFA (Multifactor Authentication)
- Microsoft always recommends blocking these protocols in tenants and enabling modern authentication.
- Credential stuffing attacks used legacy authentication in 97 percent of cases
The Importance of Blocking Legacy Authentication
Transitioning away from legacy authentication methods is a crucial step in safeguarding sensitive data and maintaining a robust security environment. By enabling a block legacy authentication policy, you demonstrate a commitment to proactive cybersecurity measures that prioritize the protection of your organization’s valuable assets.
Azure provides the following methods for blocking legacy authentication:
- Using Security default: it is a free feature of Azure that helps in protecting your organization from various attacks on identity. Microsoft manages your organization’s security settings by providing pre-configured policies for your tenant. You just have to enable it in your tenant, for new tenants, it is enabled by default.
Security default provides the following features :
- Requires MFA for all administrators
- Requires MFA registration for all users and performs MFA whenever necessary.
- Block legacy authentication protocols.
Pre-requisites:
- An Azure subscription.
- A P1 license to create a Conditional access policy
- Enable Modern Authentication in exchange
- One User ID in Azure AD to assign the policy and test it.
Build Your Career as a
Azure Cloud Architect
- Live Projects
- Resume / Interview Preparation

Boost your earning potential with Azure expertise. Explore our certified Azure Courses for a high-paying career
- Explore Azure DevOps Certification
Let’s create a conditional access policy to block Legacy authentication protocols
- Login to Azure portal https://portal.azure.com
- From All services blade search and open Azure Active directory.
- On the Azure Active directory blade under Manage click on security and then conditional access policy.
- On Conditional access policy please click on +New Policy
- On +New Policy, blade gives a name to your policy
- Go to Assignments to select users and Groups for the policy.
- Once the user blade opens Under include select users and group another tab will open there in the search box give the user name and click on select and done
Be careful in the above step do not select all users if the policy goes wrong due to human error the whole tenant will be locked out, so just select one user or always exclude the Global administrator.
- Once User assignment is done, go to cloud apps or actions and after clicking on it application tab will open, under include select All cloud apps
- Now go to conditions, under conditions select Client apps and in Client apps tab click on yes in configure tab and checkmark the legacy authentication clients i.e other clients and exchange active sync clients, click on done
- Now, go to Grant control, select Block, click on Select, and then turn policy ON and click on Create.
(Follow the numbering)
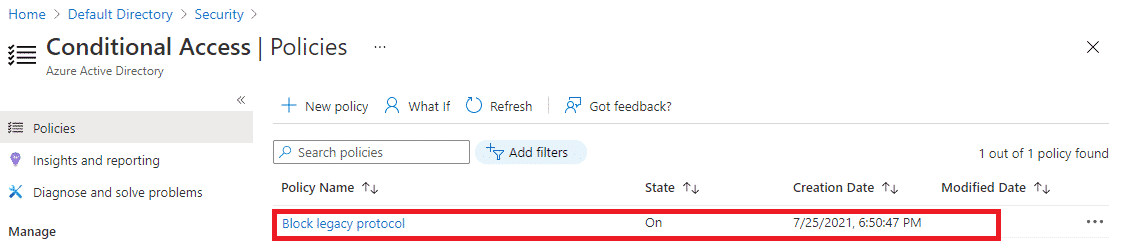
- After validation policy will get created and you can see that in the same blade.
Now it’s time to test the policy we will first log in to a browser using the test user ID and password and we should be able to login because the browser uses a Modern authentication protocol.
Let’s go to the browser
- Go to any browser and try accessing office365 with the same test user ID that you selected in CA policy as shown below:
- You can see we are able to log in as the browser uses a modern authentication protocol
We will see Azure AD sign-in logs also to have an in-depth understanding.
Go to Azure Active Directory and under Monitoring click on sign-ins and search for your user sign-in click on one log and a description of the sign-in will open go to conditional access TAB and you will see that policy is NOT applied.
Click on the policy name to check what conditions are not met and the policy detail tab will open you can see that the client app is a Browser and as stated earlier the browser uses modern authentication protocols and therefore user didn’t get blocked.
Congratulations!! You have successfully created and tested a policy for blocking legacy protocols.
Please delete the policy after testing.
Azure is really interesting to study. Experience conceptual and practical knowledge with Thinkcloudly. Explore our more free resources on Azure:
- Practice with Azure live project training.
- Read the blog over Azure live projects.
- Read Azure networking interview questions
- Read top Azure interview questions and answers.
- Don’t forget to register for our free webinars on Azure.
Important Considerations
Before blocking legacy authentication completely, it’s important to identify and address any applications or users that may still rely on these protocols. You can use Azure AD sign-in logs to identify users who are using legacy authentication protocols. You can then exempt these users from the conditional access policy or help them migrate to more secure authentication methods.
Conclusion:
With the steps outlined in this blog post, you should be able to block legacy authentication and use conditional access policies. If you’re not sure what these terms mean or want more information about how they work together then check out our other blogs here on ThinkCloudly that highlight cloud computing services like Azure Active Directory. We also offer a wide range of online courses for those who feel like their skills could do with an update!




















No comment yet, add your voice below!